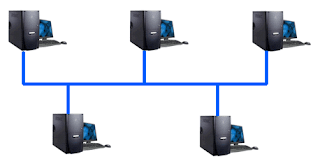
STAR TOPOLOGY
Star
networks are one of the most common computer network topologies. In its
simplest form, a star network consists of one central switch, hub or computer
which acts as a router to transmit messages. If the central node is passive,
the originating node must be able to tolerate the reception of an echo of its
own transmission, delayed by the two-way transmission time (i.e. to and from
the central node) plus any delay generated in the central node. An active star
network has an active central node that usually has the means to prevent
echo-related problems.
The star
topology reduces the chance of network failure by connecting all of the systems
to a central node. When applied to a bus-based network, this central hub
rebroadcasts all transmissions received from any peripheral node to all
peripheral nodes on the network, sometimes including the originating node. All
peripheral nodes may thus communicate with all others by transmitting to, and
receiving from, the central node only. The failure of a transmission line
linking any peripheral node to the central node will result in the isolation of
that peripheral node from all others, but the rest of the systems will be
unaffected.
Advantages
of a Star Network
- Good performance.
- Easy to set up and to expand.
- Any non-centralised failure will have very little effect on the network, whereas on a ring network it would all fail with one fault.
- Easy to detect faults
- Data Packets are sent quickly as they do not have to travel through any unnecessary nodes.
Disadvantages
of a Star Network
- Expensive to install
- Extra hardware required
- If the host computer fails the entire system is affected.
Hierarchical Topology (also known as Tree)
The type
of network topology in which a central 'root' node (the top level of the
hierarchy) is connected to one or more other nodes that are one level lower in
the hierarchy (i.e., the second level) with a point-to-point link between each
of the second level nodes and the top level central 'root' node, while each of
the second level nodes that are connected to the top level central 'root' node
will also have one or more other nodes that are one level lower in the
hierarchy (i.e., the third level) connected to it, also with a point-to-point
link, the top level central 'root' node being the only node that has no other
node above it in the hierarchy – the hierarchy of the tree is symmetrical, each
node in the network having a specific fixed number, f, of nodes connected to it
at the next lower level in the hierarchy, the number, f, being referred to as
the 'branching factor' of the hierarchical tree.
Notes:
1.) A
network that is based upon the physical hierarchical topology must have at
least three levels in the hierarchy of the tree, since a network with a central
'root' node and only one hierarchical level below it would exhibit the physical
topology of a star.
2.) A
network that is based upon the physical hierarchical topology and with a
branching factor of 1 would be classified as a physical linear topology.
3.) The
branching factor, f, is independent of the total number of nodes in the network
and, therefore, if the nodes in the network require ports for connection to
other nodes the total number of ports per node may be kept low even though the
total number of nodes is large – this makes the effect of the cost of adding
ports to each node totally dependent upon the branching factor and may
therefore be kept as low as required without any effect upon the total number
of nodes that are possible.
4.) The
total number of point-to-point links in a network that is based upon the
physical hierarchical topology will be one less that the total number of nodes
in the network.
5.) If
the nodes in a network that is based upon the physical hierarchical topology
are required to perform any processing upon the data that is transmitted
between nodes in the network, the nodes that are at higher levels in the
hierarchy will be required to perform more processing operations on behalf of
other nodes than the nodes that are lower in the hierarchy.
BUS TOPOLOGY
In bus
topologies, all computers are connected to a single cable or "trunk or
backbone", by a transceiver either directly or by using a short drop
cable. All ends of the cable must be terminated, that is plugged into a device
such as a computer or terminator. Most bus topologies use coax cables.
The
number of computers on a bus network will affect network performance, since
only one computer at a time can send data, the more computers you have on the
network the more computers there will be waiting send data. A line break at any
point along the trunk cable will result in total network failure.
Computers
on a bus only listen for data being sent they do not move data from one
computer to the next, this is called passive topology.
Advantages
- Easy to implement and extend
- Requires less cable length than a star topology
- Well suited for temporary or small networks not requiring high speeds(quick setup)
- Initially less expensive than other topologies
Disadvantages
- Difficult to administer/troubleshoot.
- Limited cable length and number of stations.
- If there is a problem with the cable, the entire network goes down.
- Maintenance costs may be higher in the long run.
- Performance degrades as additional computers are added or on heavy traffic.
- Low security (all computers on the bus can see all data transmissions).
- Proper termination is required.(loop must be in closed path).
- If one node fails, the whole network will shut down.
MESH TOPOLOGY
A Mesh
topology Provides each device with a point-to-point connection to every other
device in the network. These are most commonly used in WAN's, which connect
networks over telecommunication links. Mesh topologies use routers to determine
the best path.
Mesh
networks provide redundancy, in the event of a link failure, meshed networks
enable data to be routed through any other site connected to the network.
Because each device has a point-to-point connection to every other device, mesh
topologies are the most expensive and difficult to maintain.
Mesh
networks differ from other networks in that the component parts can all connect
to each other via multiple hops, and they generally are not mobile. Mobile
ad-hoc networking (MANET), featured in many consumer devices, is a subsection
of mesh networking.
Mesh
networks are self-healing: the network can still operate even when a node
breaks down or a connection goes bad. As a result, a very reliable network is
formed. This concept is applicable to wireless networks, wired networks, and
software interaction.
There are
three distinct generations of wireless mesh architectures. In the first
generation one radio provides both backhaul (packet relaying) and client
services (access to a laptop). In the second generation, one radio relayed
packets over multiple hops while another provided client access. This
significantly improved backhaul bandwidth and latency. Third generation
wireless mesh products use two or more radios for the backhaul for higher
bandwidth and low latency. Third generation mesh products are replacing
previous generation products as more demanding applications like voice and
video need to be relayed wirelessly over many hops of the mesh network.
RING TOPOLOGY
In a ring
topology network computers are connected by a single loop of cable, the data
signals travel around the loop in one direction, passing through each computer.
Ring topology is an active topology because each computer repeats (boosts) the
signal before passing it on to the next computer.
One
method of transmitting data around a ring is called token passing. The token is
passed from computer to computer until it gets to a computer that has data to
send.
If there
is a line break, or if you are adding or removing a device anywhere in the ring
this will bring down the network. In an effort to provide a solution to this
problem, some network implementations (such as FDDI) support the use of a
double-ring. If the primary ring breaks, or a device fails, the secondary ring
can be used as a backup.
Advantages
- Data is quickly transferred without a ‘bottle neck’
- The transmission of data is relatively simple as packets travel in one direction only.
- Adding additional nodes has very little impact on bandwidth
- It prevents network collisions because of the media access method or architecture required.
Disadvantages
- Because all stations are wired together, to add a station you must shut down the network temporarily.
- It is difficult to troubleshoot the ring.
- Data packets must pass through every computer between the sender and recipient Therefore this makes it slower.